
WordPress is one of the most popular content management systems (CMS) in the world, powering over 40% of all websites on the internet. However, its popularity also makes it a prime target for cybercriminals. One of the most common types of attacks against WordPress sites is the brute force attack.
If you can see multiple login attempts on your login page or admin page, you are under Brute Force Attack. In this article, we will explore what brute force attacks are, how they work, and most importantly, how you can prevent them from compromising your WordPress site.
- What is a Brute Force Attack?
- How Brute Force Attacks Work?
- Why Are WordPress Sites Vulnerable to Brute Force Attacks?
- How to Prevent WordPress Brute Force Attacks
- 1. Use Strong Usernames and Passwords
- 2. Limit Login Attempts
- 3. Enable Two-Factor Authentication (2FA)
- 4. Change the Default Login URL
- 5. Use a Web Application Firewall (WAF)
- 6. Disable XML-RPC
- 7. Monitor and Block Suspicious IPs
- 8. Keep WordPress Updated
- 9. Use SSL/HTTPS
- 10. Backup Your Site Regularly
- 11. Harden Your WordPress Installation
- 12. Use CAPTCHA on the Login Page
- 13. Disable Directory Indexing
- 14. Use a Secure Hosting Provider
- Conclusion
What is a Brute Force Attack?
A brute force attack is a method used by hackers to gain unauthorized access to a website by systematically trying every possible combination of usernames and passwords until the correct one is found. Since WordPress uses a login page (wp-admin or wp-login.php), attackers can automate these attempts using bots1, making it easier to crack weak credentials.
How Brute Force Attacks Work?
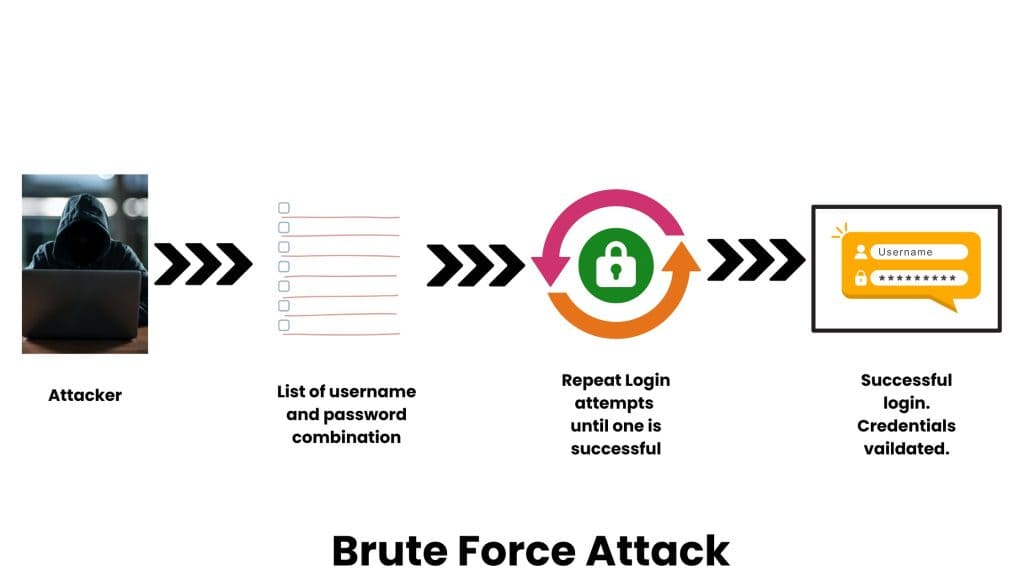
- Target Identification-> Attackers identify a WordPress site to target.
- Automated Login Attempts-> Using bots, they repeatedly try different username and password combinations.
- Access Gained-> If successful, the attacker gains access to the WordPress dashboard, potentially leading to data theft, malware injection, or defacement.
Why Are WordPress Sites Vulnerable to Brute Force Attacks?
- Default Login Page– WordPress has a default login page (
wp-adminorwp-login.php), which is easy for attackers to locate. - Weak Credentials– Many users use weak usernames (e.g. “admin”) and passwords, making it easier for attackers to guess.
- Lack of Security Measures– Many WordPress sites do not implement basic security measures, leaving them exposed to attacks.
How to Prevent WordPress Brute Force Attacks
Preventing brute force attacks requires a multi-layered approach. Below are the most effective strategies to secure your WordPress site.
1. Use Strong Usernames and Passwords
- Avoid Default Usernames-> Never use “admin” as your username. Create a unique username during installation or change it later.
- Use Strong Passwords-> Use a combination of uppercase and lowercase letters, numbers, and special characters. Consider using a password manager to generate and store complex passwords.
- Change Passwords Regularly-> Update your passwords periodically to reduce the risk of compromise.
2. Limit Login Attempts
- Install a Login Limiter Plugin-> Use plugins like Limit Login Attempts Reloaded2 or Wordfence 3to restrict the number of login attempts from a single IP address. After a set number of failed attempts, the IP will be blocked temporarily or permanently.
- Set a Reasonable Threshold-> For example, block an IP after 3-5 failed login attempts.
3. Enable Two-Factor Authentication (2FA)
- Add an Extra Layer of Security-> 2FA requires users to provide a second form of verification (e.g., a code sent to their phone) in addition to their password.
- Use a 2FA Plugin-> Plugins like Google Authenticator4 or Duo Two-Factor Authentication5 make it easy to implement 2FA on your WordPress site.
4. Change the Default Login URL
- Hide the Login Page-> By default, the WordPress login page is accessible via
/wp-adminor/wp-login.php. Changing this URL makes it harder for attackers to find. - Use a Plugin-> Plugins like WPS Hide Login 6or iThemes Security7 allow you to customize the login URL.
5. Use a Web Application Firewall (WAF)
- Block Malicious Traffic-> A WAF filters out malicious traffic before it reaches your site. It can detect and block brute force attempts, SQL injections, and other attacks.
- Cloud-Based WAFs-> Services like Cloudflare, Sucuri, or Wordfence offer WAFs that are easy to set up and highly effective.
6. Disable XML-RPC
- What is XML-RPC? XML-RPC is a feature that allows remote access to your WordPress site. Unfortunately, it can be exploited by attackers to amplify brute force attacks.
- Disable It: Use a plugin like Disable XML-RPC8 or configure your
.htaccessfile to block XML-RPC requests.
7. Monitor and Block Suspicious IPs
- Track Failed Login Attempts-> Use security plugins like Wordfence or iThemes Security to monitor login attempts and block suspicious IPs.
- Manually Block IPs-> If you notice repeated login attempts from a specific IP, block it manually via your hosting control panel or security plugin.
8. Keep WordPress Updated
- Update Core, Themes, and Plugins-> Outdated software is a common entry point for attackers. Regularly update WordPress core, themes, and plugins to patch vulnerabilities.
- Enable Automatic Updates-> Consider enabling automatic updates for minor releases to ensure your site is always running the latest version.
9. Use SSL/HTTPS
- Encrypt Data Transmission-> SSL certificates encrypt data transmitted between the user’s browser and your server, making it harder for attackers to intercept login credentials.
- Install an SSL Certificate-> Most hosting providers offer free SSL certificates through Let’s Encrypt. Ensure your site is accessible only via HTTPS.
10. Backup Your Site Regularly
- Prepare for the Worst-> Even with the best security measures, there’s always a risk of a breach. Regular backups ensure you can restore your site quickly if it’s compromised.
- Use Backup Plugins-> Plugins like UpdraftPlus9, BackupBuddy10, or Jetpack11 make it easy to schedule and store backups.
11. Harden Your WordPress Installation
- Secure wp-config.php-> Move the
wp-config.phpfile to a higher directory or restrict access to it via.htaccess. - Disable File Editing-> Add
define('DISALLOW_FILE_EDIT', true);to yourwp-config.phpfile to prevent attackers from editing theme or plugin files. - Change Database Table Prefix-> During installation, use a custom table prefix instead of the default
wp_.
12. Use CAPTCHA on the Login Page
- Prevent Bot Attacks-> Adding CAPTCHA to your login page ensures that only humans can attempt to log in.
- Install a CAPTCHA Plugin-> Plugins like Google reCAPTCHA12 or Really Simple CAPTCHA13 are easy to integrate.
13. Disable Directory Indexing
- Prevent Directory Browsing-> If directory indexing is enabled, attackers can browse your site’s directories and find sensitive files.
- Add This to .htaccess-> Add
Options -Indexesto your.htaccessfile to disable directory indexing.
14. Use a Secure Hosting Provider
- Choose a Reliable Host-> Opt for a hosting provider that prioritizes security and reliability by offering built-in features like firewalls, malware scanning, DDoS protection, and automated backups. Veeble Hosting is an excellent choice, we provide robust security measures, regular backups, and exceptional performance to ensure your website remains secure, accessible, and recoverable in any situation.
Conclusion
Brute force attacks are a serious threat to WordPress sites, but with the right precautions, you can significantly reduce the risk of being compromised. By implementing strong passwords, limiting login attempts, enabling 2FA, and using security plugins, you can create multiple layers of defense against these attacks. Additionally, keeping your site updated, using a WAF, and regularly backing up your data will ensure that your WordPress site remains secure and resilient.
Remember, website security is an ongoing process. Stay vigilant, monitor your site for suspicious activity, and continuously improve your security measures to stay one step ahead of attackers.
- Bots ↩︎
- Limit login attempt reloaded plugin ↩︎
- Wordfence ↩︎
- Google Authenticator Plugin ↩︎
- Duo Universal Plugin ↩︎
- WPS Hide Login Plugin ↩︎
- IT Themes Security Plugin ↩︎
- Disable XML-RPC Plugin ↩︎
- UpdraftPlus Plugin ↩︎
- BackupBuddy Plugin ↩︎
- Jetpack Plugin ↩︎
- Google Recaptcha Plugin ↩︎
- Really Simple CAPTCHA ↩︎
Also Read: