
This guide explains how to mask IP address on Linux using Tor and Tornet. These tools can enhance online privacy by routing your internet traffic through the Tor network and regularly changing your IP address. This can be useful for protecting your privacy from some forms of tracking and surveillance. We will cover how to connect to Tor and configure Tornet for IP address rotation.
It’s important to recognize that although these methods can enhance your privacy, they do not ensure total anonymity. We will go over the limitations of these techniques and suggest that you look into additional ways to protect your privacy.
Using these techniques for unauthorized access, network attacks, or other malicious activities is strictly prohibited, unethical, and illegal. Such actions can have serious legal consequences. This guide’s author(s) are not responsible for any misuse of this information.
Network configurations can vary significantly between Linux distributions and even between versions of the same distribution. While some commands may be similar, it’s essential to consult the documentation for your specific distribution (e.g., Ubuntu, Kali Linux, Pop!_OS, Mint) for accurate and up-to-date instructions. Always test any network changes in a non-production environment first.
Installing and Starting Tor
1. Open your terminal:
Begin by opening the terminal. This is where you’ll type your commands to summon the power of Tor to mask IP address.
2. Install the Tor package:
sudo apt install torYou might be prompted to enter your user password. Do so to proceed. A quick trip down this terminal lane, and Tor will soon be at your service.
3. Start the Tor service:
Once installed, it’s time to turn on Tor with the following command:
sudo systemctl start tor -y4. Verify that Tor is running:
To confirm that Tor is humming along nicely, type:
sudo systemctl status tor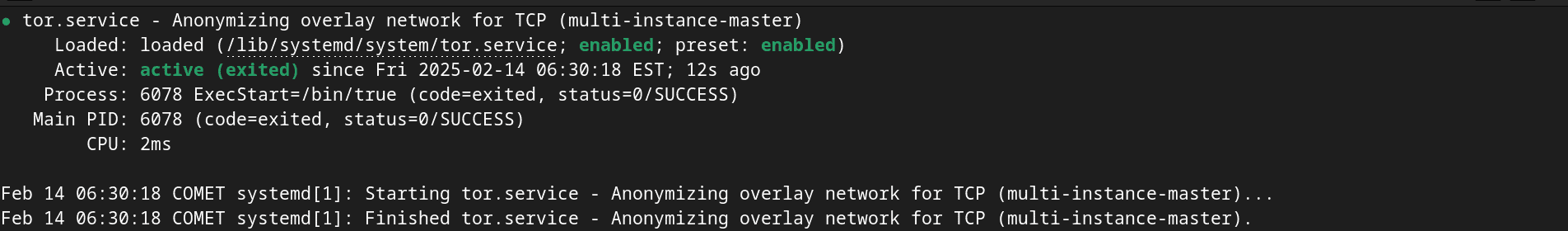
You should see that the Tor service is active and running smoothly. This is the first step towards learning how to mask IP address on any machine. A small victory dance is optional but encouraged! 🕺
Installing tornet
The next step is to arm your Linux system with tornet. This handy tool works well with Tor, enhancing your privacy strategy by helping you how to mask IP address at will.
1. Install pip if you need it:
Tornet typically gets installed via pip. Kali Linux typically comes with pip already installed. However, to ensure that pip is available on your distribution, such as Ubuntu or Debian, please check that it is installed before proceeding to the next step.:
sudo apt install python3-pip -yOr install it in a virtual environment which most of the Linux distros now accepted as a standard measure for security:
sudo apt install python3.11-venv
python3 -m venv .venv
source .venv/bin/activate
pip install tornet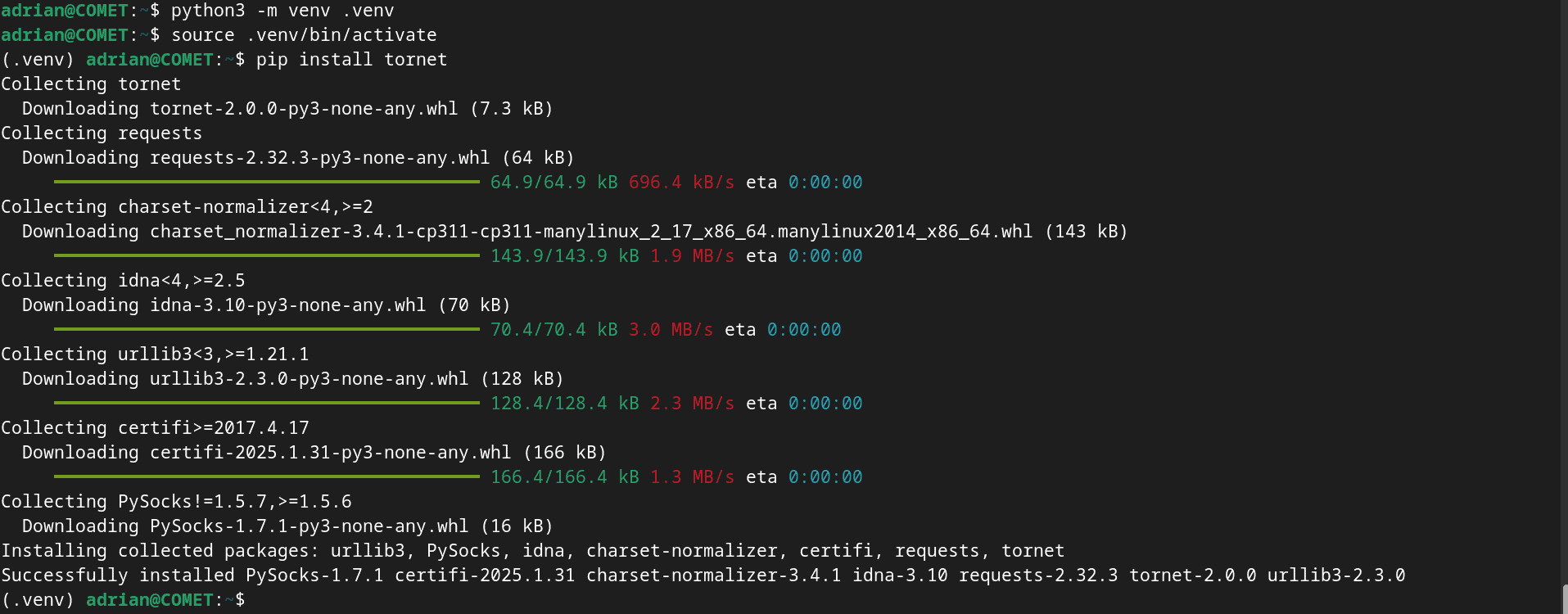
2. Install tornet:
You’re now ready to install tornet with this command:
sudo pip install tornet -yWith tornet installed, you’re one step closer to answering someone who asks how to mask IP address on Linux 😉
Configuring Your Browser
With Tor in place and tornet at your side, it’s time to set your browser to sail through this hidden network.
Firefox Browser
- Click on the menu icon on Firefox browser (usually three lines or dots) to access Settings.
- Search for PROXY in the settings search and click on Settings next to Configure how firefox connects to the internet.
- Select “Manual proxy configuration.”
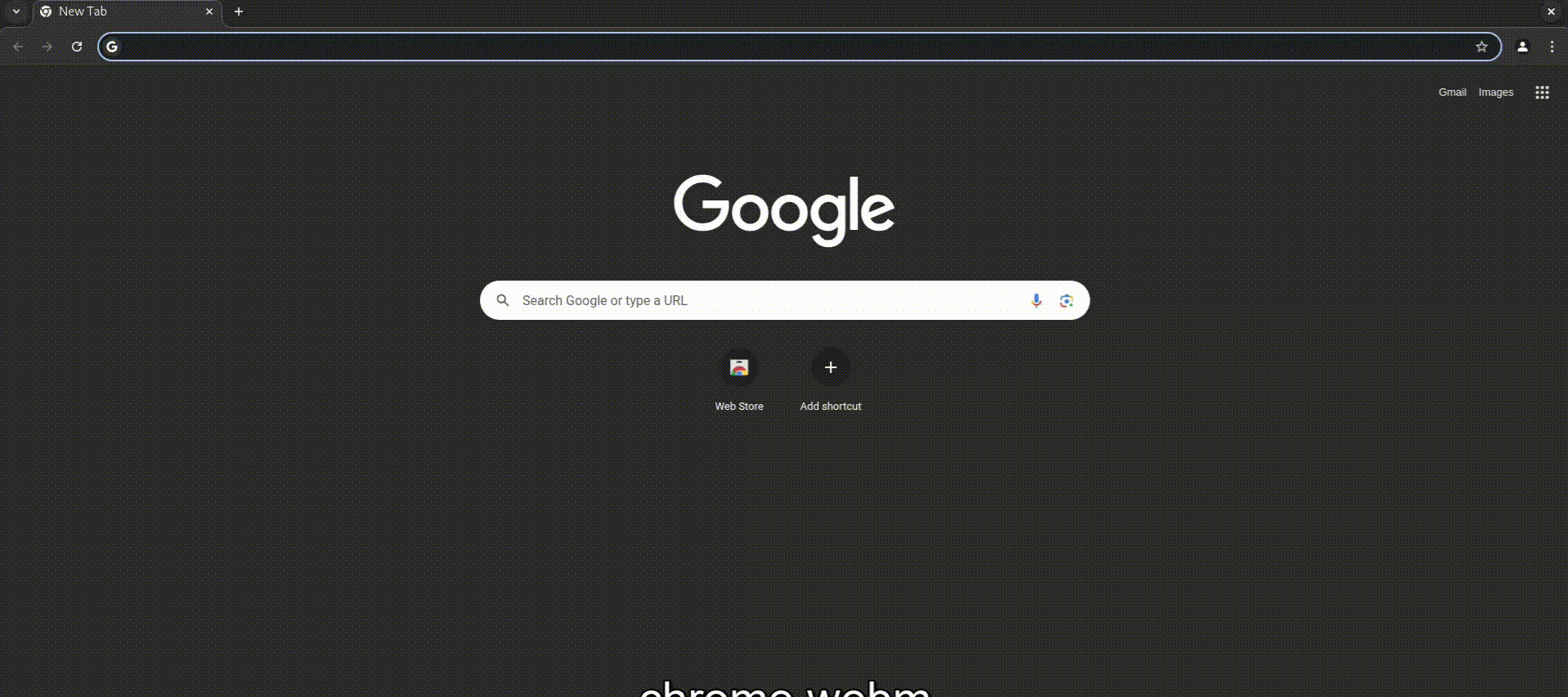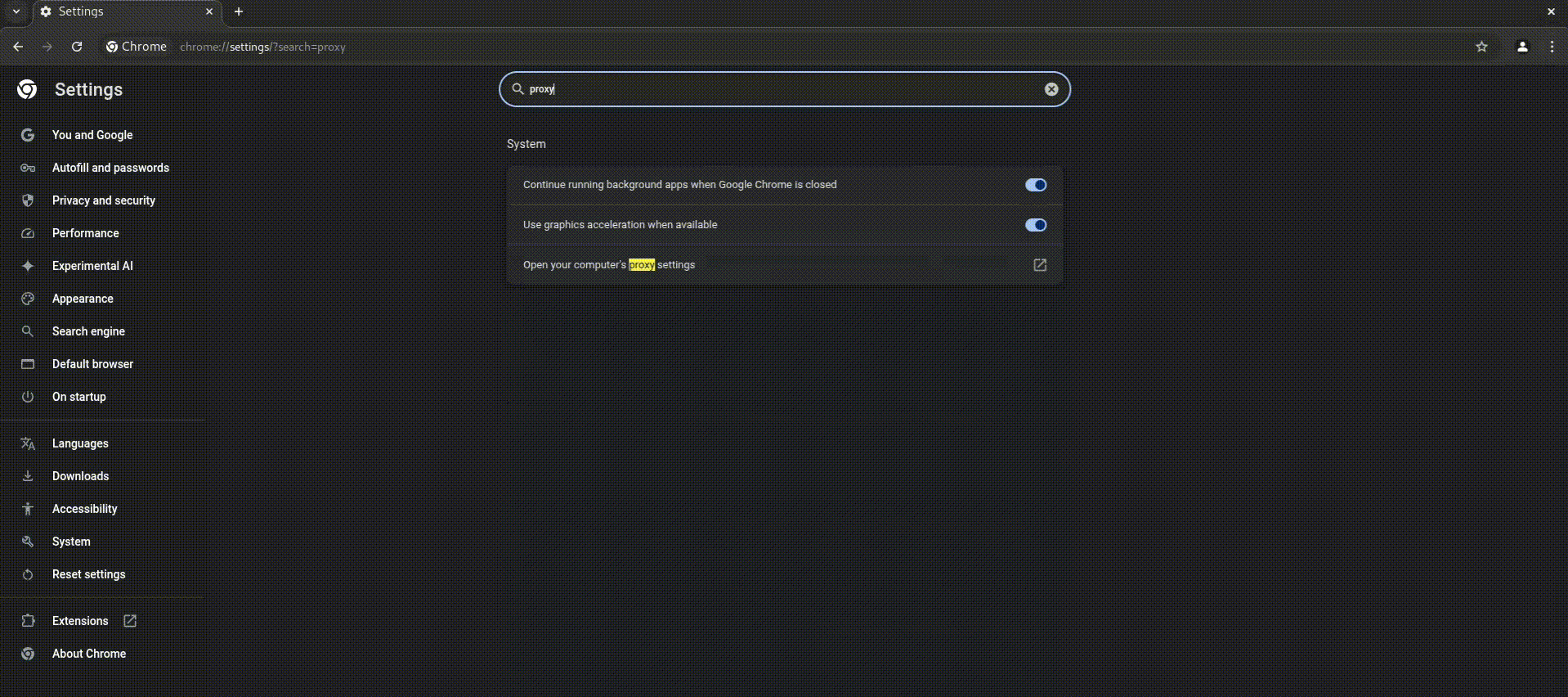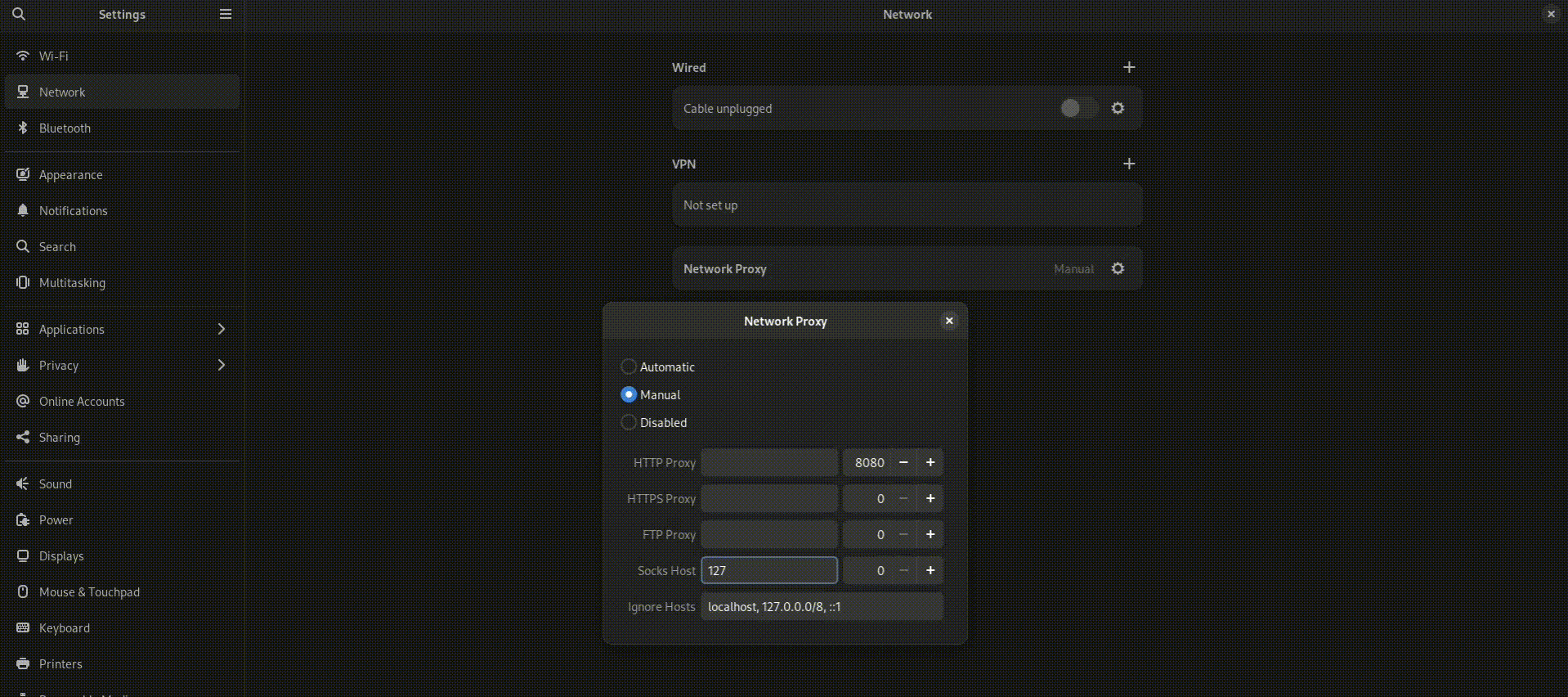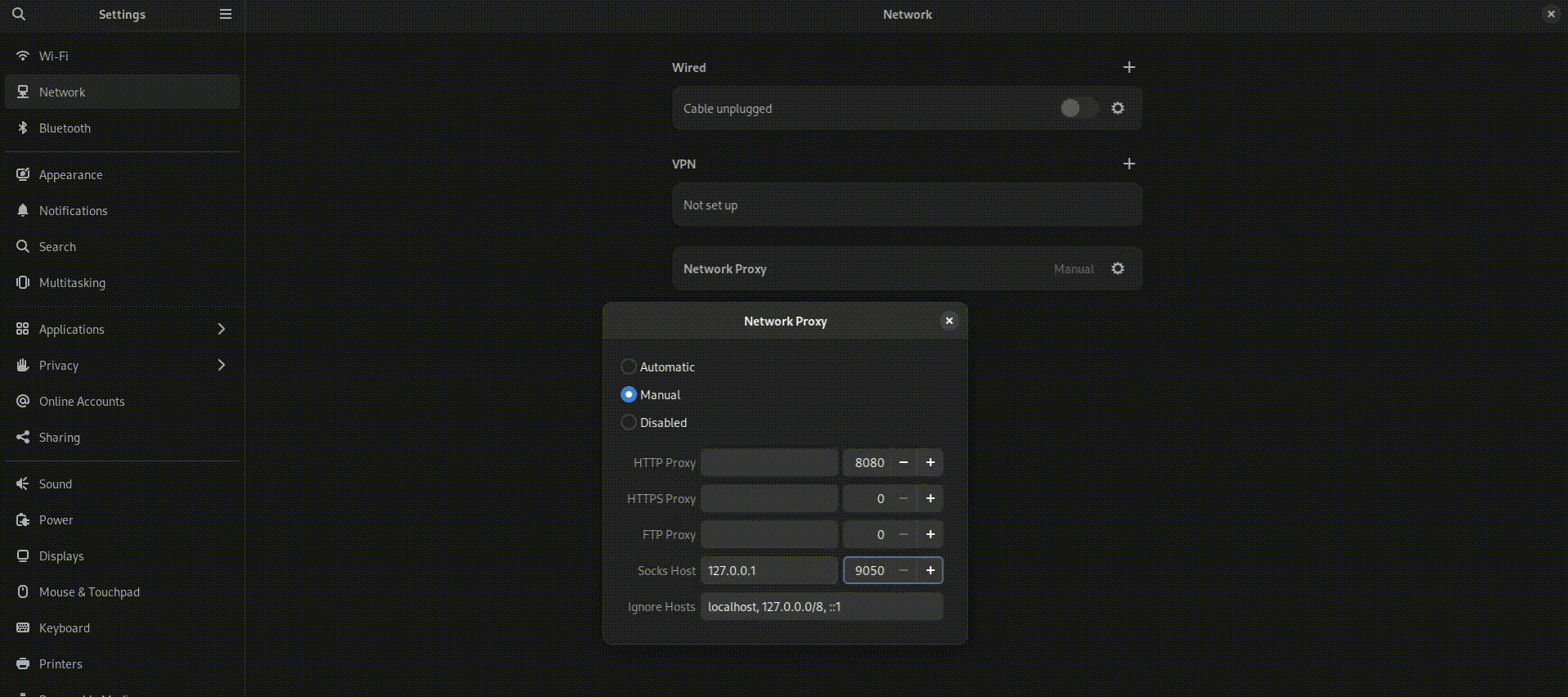
- For “SOCKS Host,” enter: 127.0.0.1
- For “Port,” enter: 9050
- Make sure you check “Proxy DNS when using SOCKS5” to prevent potential DNS leaks.
- Click “OK” to save these settings.
Chrome Browser
Chrome browser did not have any direct setup to configure the Proxy on the browser other than installing a browser extension that can manage proxy settings.
The exact steps depend on your desktop environment (GNOME, KDE, etc.). Here’s a general approach:
- GNOME (e.g., Ubuntu, Pop!_OS):
- Open “Settings.”
- Go to “Network.”
- Click the gear icon next to your network connection.
- Go to the “Proxy” tab.
- Select “Manual.”
- For “SOCKS Host,” enter 127.0.0.1.
- For “SOCKS Port,” enter 9050.
- Click “Apply.”
- KDE (e.g., Kubuntu):
- Open “System Settings.”
- Go to “Network” or “Internet & Network.”
- Look for “Proxy” settings.
- Configure a SOCKS5 proxy with Host 127.0.0.1 and Port 9050.

Using tornet to Change and MaskYour IP Address
Now, it’s time for some real magic.🪄 Changing your IP address regularly can be crucial for maintaining privacy, and tornet makes it a breeze.
1. Run tornet with specific settings:
sudo tornet --interval 3 --count 0| Option | Description |
|---|---|
| –interval 3 | This sets the interval for IP changes to every 3 seconds. It’s a quick rhythm for situations like specific testing rather than typical browsing. |
| –count 0 | This means your IP address changes will keep happening indefinitely. |
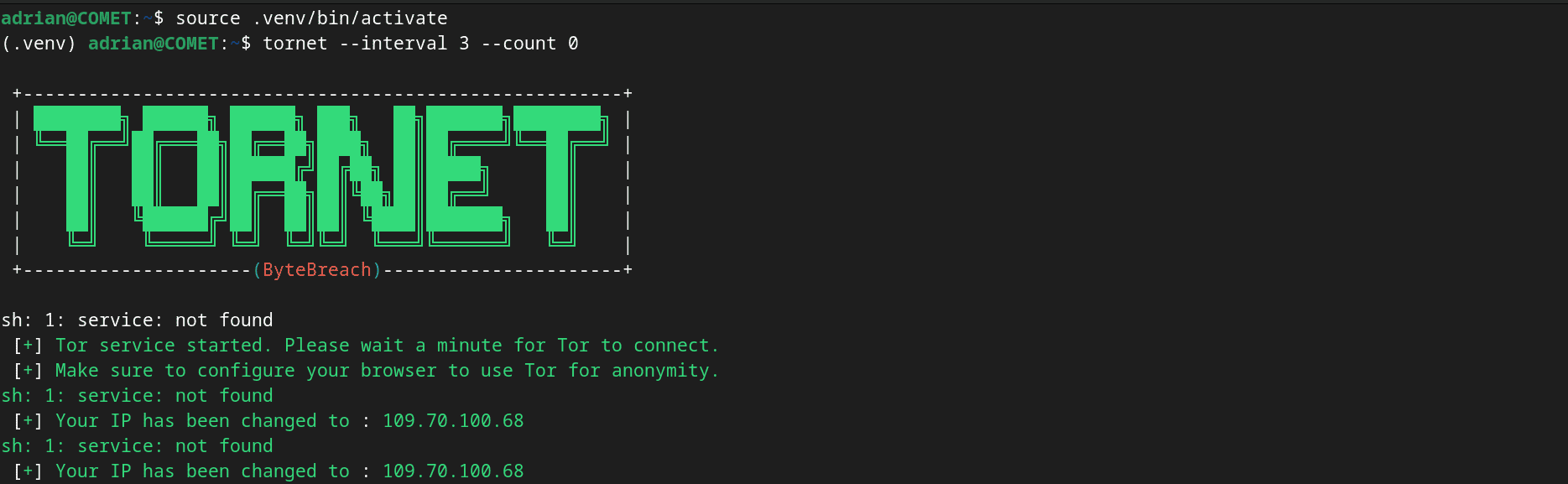
Tornet is now tuned to your specified interval, ensuring your digital concealment is adaptable and dynamic.
Verifying Your Connection
To make sure your IP is masked and you’re blending in online:
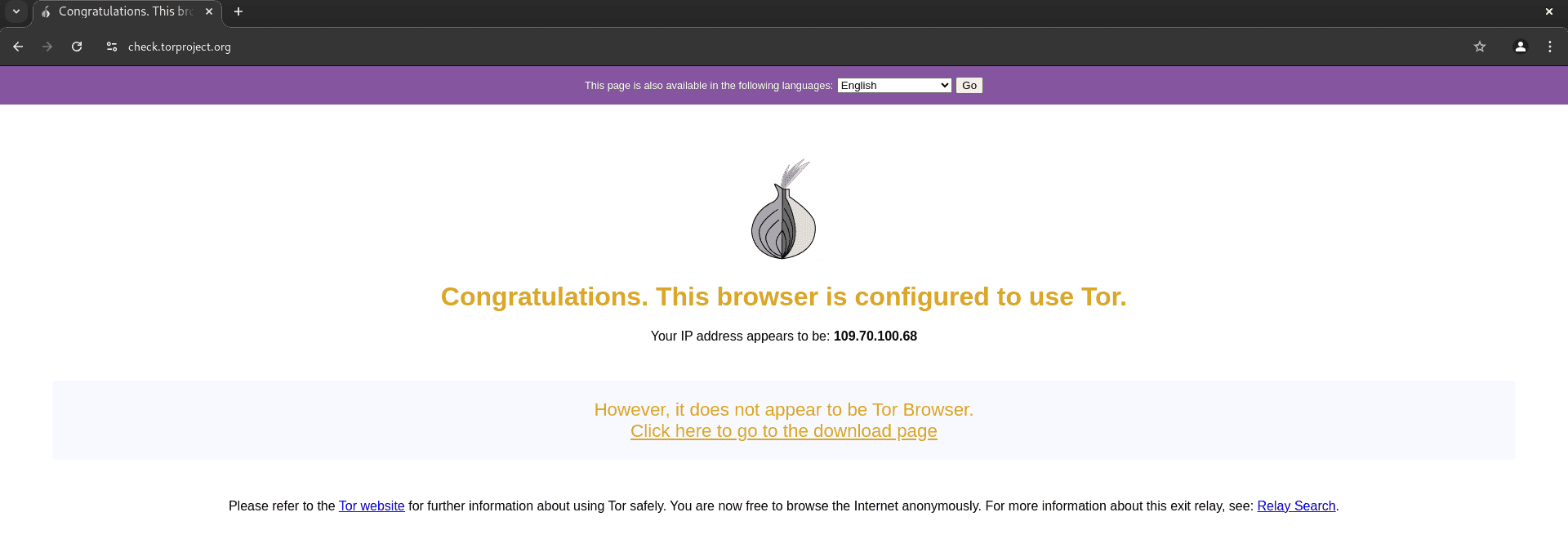
1. Check your connection:
Open your browser and visit check.torproject.org. This site will confirm whether you’re using the Tor network to access the online world.
2. Stave off DNS leaks:
Be sure to visit dnsleaktest.com to ensure your DNS requests aren’t leaking, potentially leaving a trace.
Understanding the Limitations
While Tor and tornet are effective privacy tools, they are not foolproof.
- Exit Node Vulnerabilities: Your traffic can be exposed at the exit node, always a lingering risk in privacy circles.
- Browser Fingerprinting: Skilled trackers can still potentially identify your browser settings despite masking your IP.
- Other Tracking Methods: Cookies and other trackers are another concern. Always stay vigilant.
Additional Privacy Tips
- Consider using the Tor Browser for browsing, as it’s tailored for maximum privacy.
- Be cautious with personal information shared online, as even Tor and tornet can’t protect against oversharing.
- Consider pairing with a trustworthy VPN for an extra layer of security.
- Lastly, keep everything updated — from your operating system to individual applications.
Linux users have the upper hand when it comes to privacy, but remember that it’s a constant battle like a PUBG: BattleGrounds, where threats keep changing and you need to stay alert and adapt your strategies. With the above instructions and steps, you have learned how to mask IP address on Linux and set it up on your machine. Stay informed and proactive in your privacy practices.
Also Read:
