
Granting users the ability to execute commands as the superuser (root) without entering their password can be essential in specific scenarios. Configuring the sudoers user file with the NOPASSWD directive allows for seamless execution of sudo commands without password while maintaining an organized permission structure.
In Linux server environments, managing security while ensuring seamless administrative task execution is a key challenge for system administrators. Often, there are scenarios where certain sudoers or processes need elevated privileges without being prompted for a password each time. For example, a monitoring script might require administrative privileges to gather system metrics or restart a service during downtime. In such cases, configuring the sudoers file with the NOPASSWD directive can save time and automate tasks without compromising on security—provided it is configured judiciously.
In our previous article, we have learned how to create sudo users. Now in this guide will walk you through the steps to safely configure the sudoers file to allow users or groups to execute specific commands without being prompted for a password.
Prompting for Password Without NOPASSWD Configuration
By default, Linux systems prompt users for their password whenever a sudo command is executed. This is an essential security feature that ensures only authorized users can perform administrative tasks.

If you are not a NOPASSWD sudo user, the system will always prompt for the password, as shown above. While this enhances security, it can hinder automated tasks and workflows, making the NOPASSWD option valuable in specific use cases.
Prerequisites
- Root or sudo access to the Linux system.
- Basic understanding of user permissions and sudo privileges.
- Awareness of security implications when granting password-less sudo access.
Steps to Configure Sudoers with NOPASSWD
1. Understand the Sudoers File
The sudoers file is located at /etc/sudoers and governs which users or groups have sudo privileges and under what conditions. Incorrect edits can lock you out of administrative privileges, so always proceed with caution.
2. Use visudo for Editing
To avoid syntax errors that could lead to system misconfigurations, always use the visudo command to edit the sudoers file. This utility validates the changes before applying them.
visudo3. Add a NOPASSWD Entry
Within the sudoers file, locate or add the appropriate rules under the “User privilege specification” section.
To allow a specific user (e.g., username) to run all commands without a password prompt, add:
username ALL=(ALL) NOPASSWD:ALLPlease refer the Important Security Considerations while giving NOPASSWD for all commands (ALL).
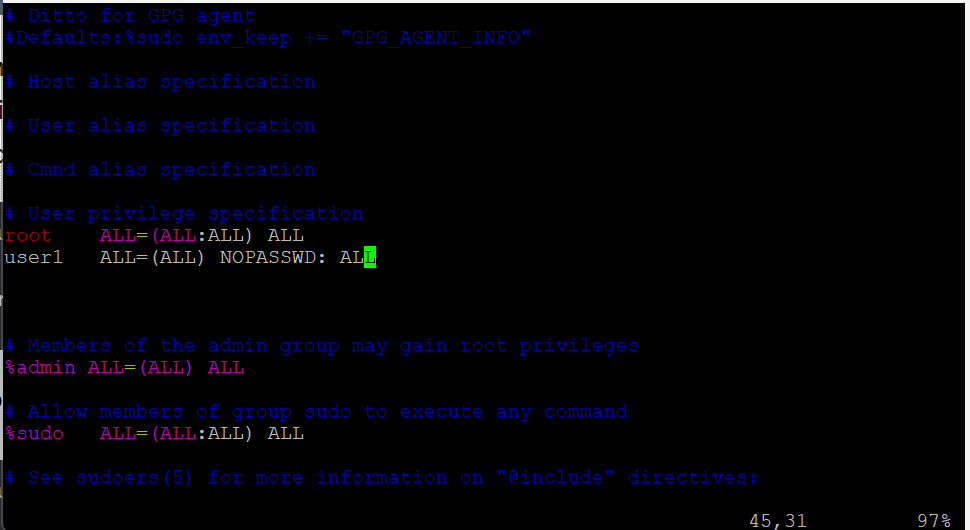
4. Save and Exit
After making the changes, save the file and exit.
Test the Configuration
To verify the configuration, switch to the user and test running any command.
su - user1
$ sudo apt install cron
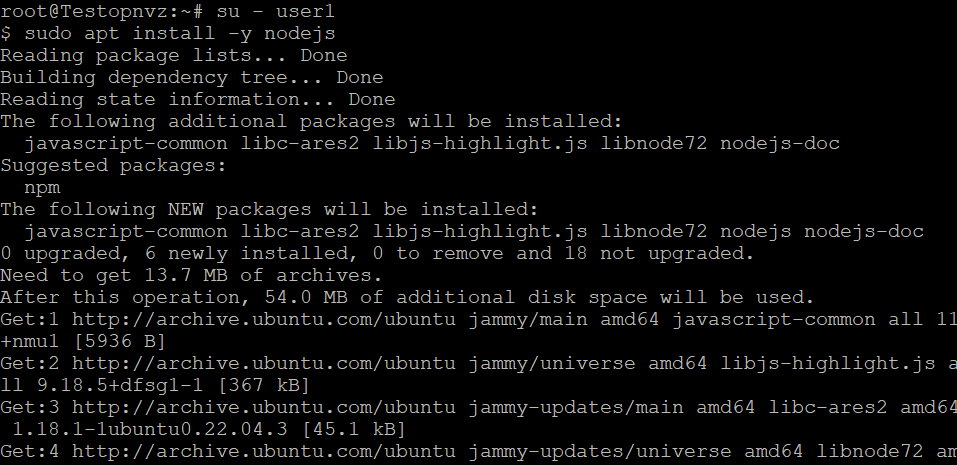
As it is configured correctly, the command is executed without prompting for a password.
Important Security Considerations
- Restrict Commands: Avoid granting
NOPASSWDfor all commands (ALL). Specify only the commands necessary for the user or group to perform their task. - Audit and Monitor: Regularly review
sudoersentries to ensure no unauthorized users or groups haveNOPASSWDprivileges. - Avoid Wildcards: Using wildcards (
*) in paths can unintentionally provide access to a broader set of commands than intended. - Test in a Controlled Environment: Test changes in a staging or non-production environment before applying them to critical systems.
Conclusion
Configuring sudoers without password is a powerful feature in Linux, enabling automated and efficient execution of administrative tasks. However, it must be used with caution to maintain system security. By granting precise permissions and regularly auditing configurations, administrators can strike a balance between convenience and security, ensuring seamless operations across their infrastructure.
Also Reads:
