I want to share my personal experience as a server administrator with Security-Enhanced Linux (SELinux), a powerful security architecture for Linux systems that gives administrators more control over who can access their servers. One of SELinux’s standout features is its ability to grant distinct permissions to various processes. Imagine you’re running a web server and need it to access your document root for reading and writing. SELinux lets you craft a policy to ensure that only the web server process can perform these actions. It’s like handing out keys to specific doors while, on the other hand, keeping others securely locked. However, this selective access control ensures that only authorized individuals can enter, thereby enhancing security.
Unleashing the Power of SELinux
SELinux operates on the concept of Mandatory Access Controls (MAC), which go beyond the traditional Discretionary Access Control (DAC) you might be familiar with. Discretionary Access Control (DAC) empowers users and processes to manage their resource access. In contrast, SELinux flips the script by placing restrictions on users and processes based on rules and policies set by the system administrator. It’s not your typical security measure; it’s a higher tier of access control.
You might wonder how SELinux accomplishes this feat. Think of it as a virtual bouncer stationed at the entrance to your system, effectively ensuring that it only allows authorized individuals to pass through the door. SELinux processes files that administrators pre-approve, thereby preventing any unauthorized access and, as a result, bolstering your system’s security.
For most system users, SELinux operates quietly in the background, seamlessly safeguarding your system. Moreover, its presence won’t disrupt your daily tasks.The beauty of SELinux lies in its flexibility – you have the power to customize your security policies, determining the level of strictness or leniency that best suits your server environment.
Enhancing your server’s security with SELinux is a wise decision. Furthermore, it’s like having an invisible fortress around your Linux system, allowing you to define who gains access and who remains locked out. Moreover, the power of SELinux lies in its ability to bolster your defenses, ensuring that your server remains impenetrable to unauthorized intruders.
The decision making process for SELinux
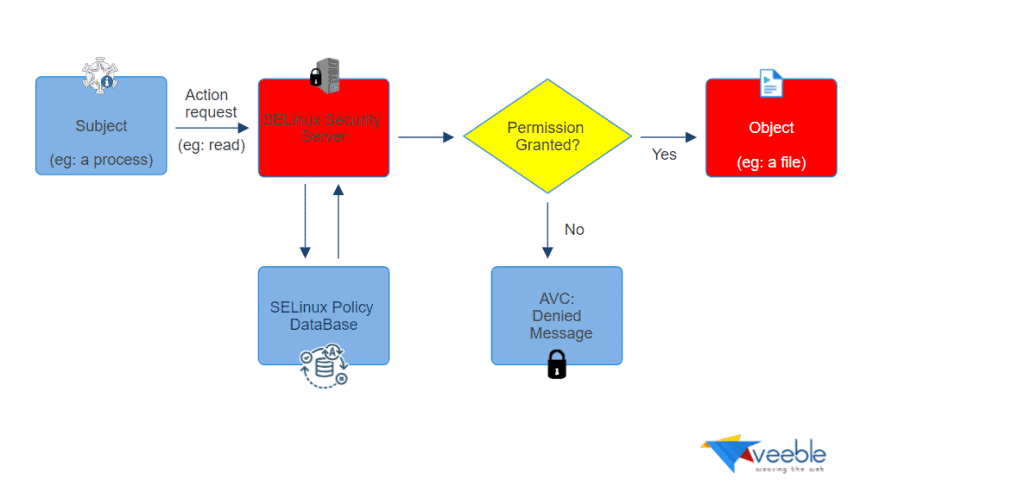
When an application (subject) attempts to access a file (object), the kernel’s policy enforcement server checks an access vector cache (AVC). This cache stores subject and object permissions, ensuring secure access.
Consequently, if the AVC data cannot make a decision, the system forwards the request to the security server, which then searches a matrix for the security context of the application and the file. Permission is then granted or denied, and if denied, it issues an avc: denied message. The installed policy applies the security context of subjects and objects, providing information to populate the security server’s matrix.
SELinux Modes
For troubleshooting and configuration, SELinux offers three different modes, each serving a distinct purpose:
1. Enforcing Mode:
For example, by implementing security measures, it can effectively prevent a web server from reading files with a context not explicitly allowed.
2. Permissive Mode:
3. Disabled Mode:
Configuration File and Checking the Current Mode
To configure SELinux and check its current mode, you can access the SELinux configuration file and use the “getenforce” command:
Configuration File: You can open the SELinux configuration file with your preferred text editor. The configuration file is typically located at /etc/selinux/config.
# vi /etc/selinux/config.
Checking the Current Mode: To determine the current SELinux mode, execute the “getenforce” command:
# getenforce
Understanding SELinux modes and the decision-making process is crucial for effectively managing and troubleshooting SELinux on your system. Additionally, it empowers you to control access and enhance the security of your Linux environment.
