Red Hat Product Security is aware of a ‘buffer overflow vulnerability. This is what affects the Floppy Disk Controller (FDC) emulation. It is implemented in the QEMU component of the KVM/QEMU and Xen hypervisors. The vulnerability is now called VENOM and it was discovered by Jason Geffner of CrowdStrike, Inc. The vulnerability is said to have an important impact.
What is QEMU?
QEMU is a generic and open source machine emulator and virtualizer. It is incorporated in some Red Hat products as a foundation and hardware emulation layer. This is used for running virtual machines under the Xen and KVM/QEMU hypervisors.
Impact
As mentioned before, using this vulnerability the privileged guest user in the host can destroy the guest or can execute arbitrary code on the host. And it may be with the privileges of the host’s QEMU process corresponding to the guest. Please note that this issue is exploitable even if the guest does not explicitly have a virtual floppy disk configured and attached. The problem exists in the Floppy Disk Controller. It is the one initialized for every x86 and x86_64 guest. And is regardless of the configuration and cannot be removed or disabled.
As of now, there is no known exploit that would make use of this vulnerability. The sVirt and seccomp functionalities are used to restrict the host’s QEMU process privileges. The resource access might mitigate the impact of successful exploitation of this issue. Avoid granting untrusted users administrator privileges within guests can prevent the issue to some extent.
The interesting fact is that the flaw does not require the floppy device to be present in /dev/ within the guest. This is because the Floppy Disk Controller (FDC) is still present in the system. User-level access to a guest with sufficient permissions to talk to FDC I/O ports (i.e. the root or a privileged user on Linux or virtually any user on a Windows guest) is all that is required to exploit this flaw. To mitigate the overall risk of this vulnerability, only grant privileged guest access to trusted users.
All Red Hat products that include QEMU are vulnerable to this flaw. Affected Red Hat products are the following: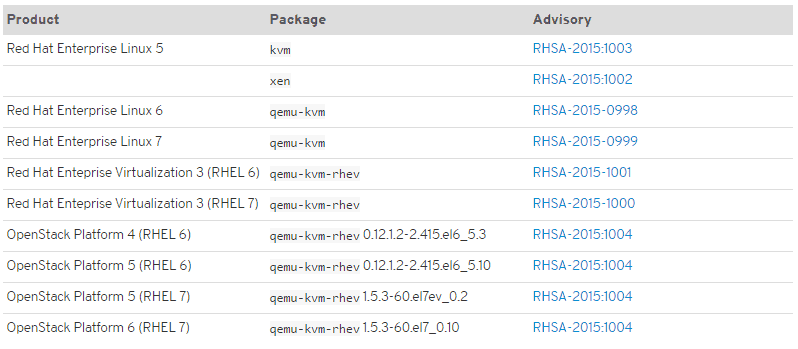
Resolution
There are a few steps to eliminate the possibility of exploitation. Install the updated QEMU, KVM, or Xen packages. This is available through the advisories listed in the above table.
You can install the updates using the yum package manager as follows:
root# yum update
If you want to update the QEMU package (or the relevant package for your system) and its dependencies, use, for example:
root# yum update qemu-kvm
Following the update, power off and start up the guests (virtual machines) for the update to take effect. It is also possible to migrate guests away from the affected host, update the host, and then migrate the guests back. Please note that it is not enough to restart the guests because a restarted guest would continue running using the same (old, not updated) QEMU binary.
That’s all!
