In today’s ever-evolving digital landscape, safeguarding the security of your Linux Virtual Private Server (VPS) is of utmost importance. You need to decide what security measures are needed, but remember, this isn’t a one-time job.
The task of VPS hardening is a never-ending job.You have to regularly check and make your VPS secure. VPS security is an ongoing task, and it’s important to learn about the necessary settings and steps to keep your server safe. The digital world keeps changing, so safeguarding your VPS is not just a choice but a necessity.
This article is intended to familiarize you with 15 important and common security measures to implement in a Linux server environment.
- Configure Firewall
- Close Unnecessary Ports
- Change Default Listening SSH Port
- Strong Password Policy
- Set Up a VPN for Your VPS
- Create a non root user and Disable password and Root Logins
- Monitor Server Logs
- Generating a PEM Key and Connecting to a Linux Server
- Encrypt Disk in via CLI
- Disable unused services
- Enhancing Linux Security with SELinux: 3 Modes to know
- PHP Versioning
- Strengthening SSH Security with Google Authenticator’s Two-Factor Authentication
- Keep software up to date
- Protecting Files, Directories
1. Configure Firewall
Configuring the firewall is a fundamental step in fortifying the security of your VPS. The firewall acts as a crucial barrier, allowing you to control incoming and outgoing network traffic, safeguarding your VPS against potential threats. By implementing a well-configured firewall, you not only establish a safeguard for your VPS but also gain control over which services and ports are accessible, fortifying your server against unauthorized access and potential vulnerabilities.
Install Firewalld (if not already installed):
[root@ervintest ~]# dnf install firewalldStart and Enable Firewalld:
[root@ervintest ~]# systemctl enable firewalld
[root@ervintest ~]# systemctl start firewalld
[root@ervintest ~]# systemctl status firewalld
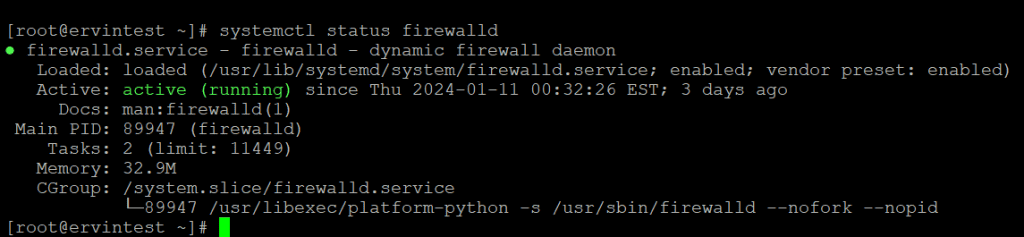
View Available Zones:
Firewalld uses predefined zones. To view available zones, use:
[root@ervintest ~]# firewall-cmd --get-zones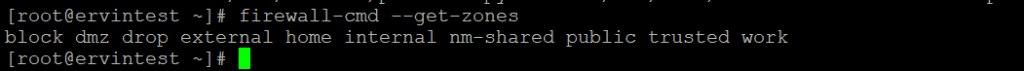
Set Default Zone (Optional):
You can set a default zone based on your network environment.
[root@ervintest ~]# firewall-cmd --set-default-zone=publicList Allowed Services:
To see a list of allowed services, use:
[root@ervintest ~]# firewall-cmd --list-services2. Close Unnecessary Ports
Now you would are already familiar with the zones of the Firewalld, now we can learn to manage ports or services in various zones.
[root@ervintest ~]# firewall-cmd --permanent --zone=public --add-port=80/tcpOr
# firewall-cmd --permanent --zone=public --add-service=http#firewall-cmd --reloadSame as enabling ports, we can also disable unwanted ports.
#firewall-cmd --permanent --zone=public --remove-port=80/tcp# firewall-cmd --permanent --zone=public --remove-service=httpTo get the list of allowed services:
#firewall-cmd --list-services3. Change Default Listening SSH Port
Changing the default SSH port involves modifying the SSH daemon configuration file. Follow these steps to change the default SSH port:
vi /etc/ssh/sshd_configWithin the configuration file, look for the line that specifies the SSH port.
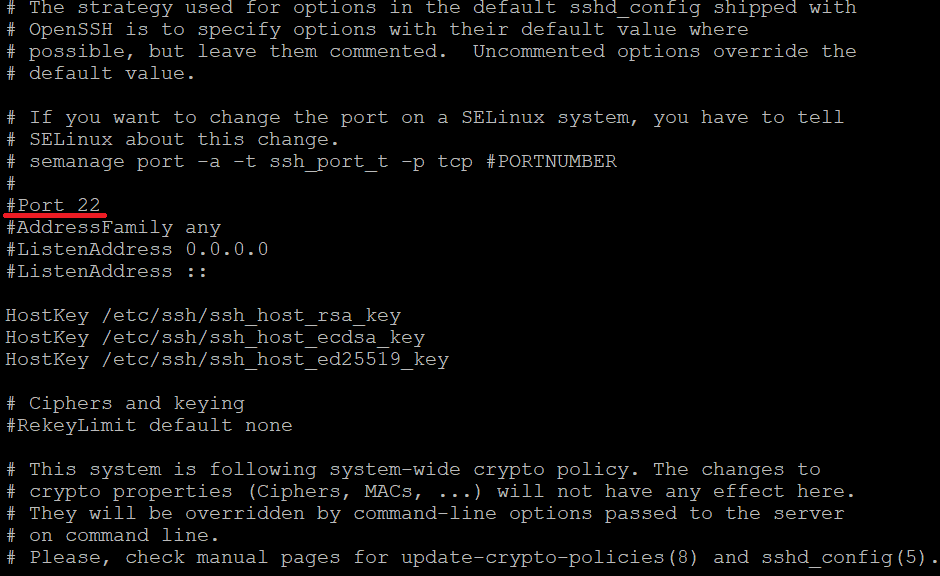
-> Uncomment the line (remove # at the beginning) and change the port number to your desired value.
-> Choose a port number that is not commonly used and is not in conflict with other services.
4. Strong Password Policy
In establishing robust security measures for Linux user accounts, implementing a strong password policy is a fundamental component. An effective password policy involves configuring the Pluggable Authentication Modules (PAM) and enforcing settings that govern password strength, expiration, and other security aspects. By defining parameters such as minimum length, character class requirements, and aging policies, administrators can enhance the resilience of user accounts against unauthorized access. Regular audits, communication of policy guidelines to users, and periodic updates ensure the ongoing efficacy of the password policy, contributing significantly to the overall security posture of the Linux system.
5. Set Up a VPN for Your VPS
Setting up a Virtual Private Network (VPN) for your Virtual Private Server (VPS) is a crucial step in enhancing security, especially when accessing your server over public networks. A VPN creates a secure, encrypted connection, safeguarding your data from potential interception and ensuring a private communication channel. To establish a VPN for your VPS, you typically need to install and configure VPN server software, such as OpenVPN or WireGuard, on your server. Following installation, you’ll generate cryptographic keys, configure user authentication, and set up client devices to connect securely to your VPS. Utilizing a VPN adds an extra layer of protection, making it more challenging for unauthorized entities to intercept your traffic and enhancing overall VPS security.
You can refer the detail steps of setting a VPN using OpenVPN here.
6. Create a non root user and Disable password and Root Logins
To enhance the security of your Linux server, it is recommended to create a non-root user with sudo privileges, disable password logins, and prohibit root logins.
By establishing a dedicated non-root user and restricting root access via SSH, administrators mitigate the risk of unauthorized access and potential security threats. This approach encourages the use of a standard user account with limited privileges, reducing the likelihood of unintended system modifications and bolstering the overall security framework of the VPS environment. We have already discussed the detail steps of creating a non root user and Disable password and Root Logins. You can refer the details here.
7. Monitor Server Logs
Monitoring server logs is a critical aspect of maintaining a security to Virtual Private Server (VPS) environment. Server logs provide valuable insights into system activities, potential security incidents, and overall performance. Regularly reviewing logs allows administrators to identify abnormal behavior, detect security breaches, and troubleshoot issues promptly. Key logs to monitor include system logs (syslog), authentication logs, and application-specific logs. Implementing log monitoring tools and establishing alert mechanisms further enhance the ability to proactively respond to security threats. By staying vigilant and proactive in log analysis, administrators can maintain a robust security posture for their VPS, ensuring the early detection and mitigation of potential risks.
8. Generating a PEM Key and Connecting to a Linux Server
Generating a PEM (Privacy Enhanced Mail) key and establishing a secure connection to a Linux server is a fundamental process in securing remote access. PEM keys, often used for SSH (Secure Shell) authentication, provide a robust alternative to password-based logins. To initiate this process, users typically generate a key pair – a private key kept on their local machine and a corresponding public key uploaded to the Linux server. This secure handshake ensures encrypted communication during remote sessions, significantly enhancing the server’s defense against unauthorized access. The subsequent connection, validated by the PEM key pair, ensures a seamless and secure interaction with the Linux server, contributing to a robust security posture. The detailed steps to generate a PEM key and use it to connect to a server , Kindly refer this article.
9. Encrypt Disk in via CLI
Encrypting a disk via the command line is a crucial step in securing sensitive data on a Linux system. To encrypt a disk, you can use the cryptsetup utility, which is commonly available on most Linux distributions. Disk encryption protects against unauthorized access by encrypting the contents of the disk, ensuring that even if physical access is gained, the data remains inaccessible without the appropriate decryption key. This process involves setting up a passphrase or keyfile for decryption, adding an extra layer of protection to prevent unauthorized users from accessing critical information stored on the disk. To boost your data security by encrypting your disk in Ubuntu, Kindly refer this article.
10. Disable unused services to enhance VPS security
Disabling unused services on a system is a fundamental security practice that helps minimize potential attack surfaces and reduce the overall risk of vulnerabilities. Unused services, often running in the background, can pose security risks if not properly configured and maintained. To enhance system security:
Identify Unused Services: Audit the services running on your system using commands
systemctl list-units --type=service
or chkconfig --listIdentify services that are unnecessary for your specific use case.
Stop and Disable Services: Use the appropriate commands to stop and disable unused services.
Syntax to stop a service
systemctl stop <service_name> To disable it, preventing it from starting at boot
sudo systemctl disable <service_name>11. Enhancing Linux Security with SELinux
Security-Enhanced Linux, or SELinux, is a set of kernel modifications and user-space tools that implement mandatory access controls (MAC) to strengthen the security of Linux systems. Developed by the National Security Agency (NSA) in collaboration with the open-source community, SELinux goes beyond traditional discretionary access controls (DAC) by enforcing policies that restrict and control the actions of processes and users.
While SELinux enhances security, it may require careful configuration and tuning to avoid interference with legitimate operations. Administrators need to be familiar with SELinux policies and contexts to effectively manage and troubleshoot issues. SELinux is commonly found in Red Hat-based distributions like Fedora, CentOS, and RHEL, but it can be enabled or disabled based on system requirements and security policies. To know more details about SELinux , kindly refer this article
12. PHP versioning
PHP versioning refers to the practice of managing and identifying different releases or versions of the PHP programming language. Each PHP version represents a specific set of features, improvements, bug fixes, and sometimes backward-incompatible changes. The PHP development team follows a release cycle to introduce new versions, that ensuring the language remains up-to-date, secure, and compatible with evolving web development practices.
Developers and system administrators always need to stay informed about PHP version releases, assess the impact of changes on their projects, and plan for timely upgrades to benefit from performance improvements, security patches, and new language features.
13. Strengthening SSH Security with Google Authenticator’s Two-Factor Authentication
Strengthening SSH security with Google Authenticator’s Two-Factor Authentication (2FA) adds an additional layer of protection to remote access, enhancing resistance against unauthorized login attempts. Google Authenticator generates time-based one-time passcodes (TOTPs) that users must enter alongside their regular password during SSH authentication. This dynamic authentication method significantly reduces the risk of unauthorized access even if login credentials are compromised. The implementation involves configuring the OpenSSH server to support 2FA, installing and configuring the Google Authenticator PAM module, and then enabling 2FA for specific users. By seamlessly integrating Google Authenticator’s Two-Factor Authentication (2FA) into SSH, administrators fortify the security of their systems, establishing a more robust defense against potential threats. This additional layer of protection enhances resilience, ensuring that even if login credentials are compromised, the dynamic authentication process significantly reduces the risk of unauthorized access. To understand the detailed steps of this kindly refer this article.
14. Keep software up to date enhances the security of VPS
Keeping software up to date is a fundamental practice in maintaining the security, stability, and performance of computer systems. Regularly updating software, including the operating system, applications, and libraries, provides several key benefits like :
- Security Patches: Software updates often include security patches that address vulnerabilities discovered since the previous release. By keeping software up to date, users ensure that their systems are protected against known security threats.
- Bug Fixes: Updates typically include bug fixes that address issues and improve the overall stability and functionality of the software. Updating helps prevent crashes, errors, and unexpected behavior.
- Performance Improvements: Software updates may introduce optimizations and performance enhancements. Users can benefit from improved speed, efficiency, and resource utilization by staying current with the latest releases.
- Compatibility: As software evolves, updates help maintain compatibility with the latest hardware, devices, and standards. Ensuring compatibility with the latest technologies is essential for a seamless user experience.
- Feature Enhancements: Updates often bring new features, functionalities, and improvements. Keeping software up to date allows users to access the latest tools and capabilities provided by the developers.
Whether managing a personal computer or overseeing an entire IT infrastructure, prioritizing regular software updates is a proactive measure to ensure a secure, efficient, and reliable computing environment.
15. Protecting Files, Directories
Protecting files and directories is crucial for securing sensitive data on a Linux system. Utilizing file permissions and ownership, administrators can control access levels, ensuring that only authorized users or processes have the right to read, write, or execute specific files. Setting appropriate permissions using commands like chmod and chown helps prevent unauthorized modifications and data breaches. Additionally, encrypting sensitive files and employing secure file transfer protocols such as SFTP or SCP adds an extra layer of protection. Regularly auditing and monitoring file permissions, coupled with restricting access to critical directories, forms a robust defense against unauthorized access and ensures the integrity of the system’s file structure.
